How familiar are you with what the blockchain is made of and how it works? Would you like a great reference article to refer back to when you need to clarify what is a Layer 1 project vs. a Layer 2 project? Where did the Layer 3 projects come from and why? This in-depth article is designed to provide you with a solid basic understanding of how the blockchain works and why we need these 3 layers. As a bonus, we reference similar articles and provide you with a downloadable PDF for each layer. Are you ready to get started?
Understanding The Layers Of The Blockchain
If you’ve looked into cryptocurrencies or blockchain in any way, you’ve probably come across terms like layer one and layer two protocols. Are you curious about what these layers are and why they exist? Let’s discuss blockchain layer architecture in this article.
Blockchain technology is a one-of-a-kind mix of several current technologies — cryptography, game theory and so on — with a wide range of possible applications such as cryptocurrencies. Encoding and decoding data is a mathematical and computational discipline known as cryptography. The study of the mathematical models of strategic interaction among rational decision-makers is known as game theory. Blockchain eliminates intermediaries, lowers costs and improves efficiency by bringing transparency and security.
Without the oversight of a central authority, distributed ledger technology (DLT) keeps information verified by cryptography among a group of users who agreed through a predetermined network protocol. Combining these technologies fosters trust between people or parties who would otherwise have no motive to do so. They make it possible for blockchain networks to exchange value and data between users securely.
Due to the lack of a centralized authority, blockchains must be very safe. They must also be extremely scalable to handle increasing users, transactions, and other data. Layers were born out of the requirement for scalability concurrent to the preservation of top-notch security.
What Is Blockchain Scalability?
The phrase “scaling” in blockchain technology refers to an increase in the system throughput rate, which is measured in transactions per second. With the widespread adoption of cryptocurrencies in everyday life, blockchain layers are now required to improve network security, recordkeeping, and other functions.
The number of transactions handled by a system per second is referred to as “throughput.” While Visa’s VisaNet electronic payment network can process over 20,000 transactions per second, Bitcoin’s (BTC) main chain cannot handle more than seven transactions per second.
The blockchain is the first layer in a decentralized ecosystem. Layer two is a third-party integration used in conjunction with layer one to enhance the number of nodes and, as a result, system throughput. Many layer two blockchain technologies are currently being implemented. Smart contracts are used in these solutions to automate transactions.
Blockchain developers are attempting to broaden the scope of blockchain management as Bitcoin becomes a more significant force in the commercial world. They hope to reduce processing times and increase TPS by developing blockchain layers and optimizing layer two scalability.
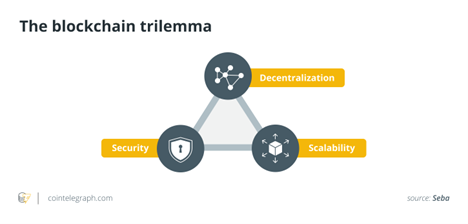
The Blockchain Trilemma
The blockchain trilemma refers to the commonly held notion that, in terms of decentralization, security and scalability, decentralized networks can only provide two of the three benefits at any given time.
Computer scientists devised the consistency, availability, and partition tolerance (CAP) theorem in the 1980s to express possibly the most significant of these difficulties. The CAP theorem states that decentralized data storage, such as blockchain, can only satisfy two of the three guarantees mentioned above simultaneously.
This theorem has evolved into the blockchain trilemma in the context of the current distributed networks. The widely held notion is that public blockchain infrastructure must sacrifice security, decentralization, or scalability.
As a result, the holy grail of blockchain technology is to create a network with impenetrable security over a broadly decentralized network while also handling internet-scale transactional throughput.
Before delving into the trilemma’s dynamics, let’s define scalability, security and decentralization in general terms:
- The blockchain’s scalability refers to its ability to handle a higher volume of transactions.
- Security refers to the ability to secure data on the blockchain from various types of assaults and the blockchain’s defense against double-spending.
- Decentralization is a type of network redundancy that ensures that the network is not controlled by fewer entities.
The Interplay Among Scalability, Security, And Decentralization
To settle a transaction, the network must first agree on its validity. The agreement may take some time if the system has a large number of members. As a result, we can show that scalability is inversely proportional to decentralization when security parameters are identical.

Now, assuming that two proof-of-work blockchains have the same degree of decentralization and consider security to be the blockchain’s hash rate. The confirmation time decreases as the hash rate rises, and scalability rises as security improves. As a result, scalability and security are proportionate with constant decentralization.

As a result, a blockchain cannot optimize for all three desired features simultaneously, forcing it to make trade-offs. Ethereum is the most recent example of the trilemma in action. The Ethereum platform has seen a boom in usage due to the growth of decentralized finance (DeFi) applications this summer. Ethereum can only grow to a certain point.
Due to the increased demand, transaction fees have risen to the point where some people cannot engage with the blockchain. Increased Ethereum fees are an example of the trilemma, as we can see that Ethereum did not scale without sacrificing security or decentralization.
The focus of Ethereum was on decentralization and security, with the number of transactions per second being limited (scalability). To encourage miners to prioritize their transactions, users paid higher fees. Similarly, decentralization and security have taken precedence over scalability in Bitcoin.
It’s no secret that the scalability of blockchains like Bitcoin and Ethereum is currently limited. Therefore, a global community of start-ups, corporations and technologists is working frantically on layer one and layer two solutions to solve the blockchain trilemma.
Layer one blockchain networks are designed for speed, security and expansion. Layer two refers to technology enhancements and products that can be utilized to expand the scalability of existing blockchain networks. Getting the perfect balance between the two layers might be a game-changer for blockchain adoption and the expansion of decentralized networks.
Developers are approaching the issue from a variety of perspectives. The increased block size in Bitcoin Cash (BCH) was an attempt to improve Bitcoin’s scalability. However, there is no evidence that it is becoming more popular.
Bitcoin is seeking to tackle the problem by adding a layer to the existing blockchain layer. The layer two solutions will bundle numerous transactions together and only query the base layer blockchain once in a while, according to the idea behind scaling solutions. Ethereum is taking a hybrid approach, with sharding scaling the base layer blockchain and the community anticipating several layer two solutions to boost throughput even further.
The Layered Structure Of The Blockchain Architecture
In the case of blockchain architecture’s distributed network, each network participant maintains, authorizes, and updates new entries. A collection of blocks with transactions in a specific order represents the structure of blockchain technology. These lists can be saved as a flat file (in txt format) or a simple database. Blockchain architecture can take public, private or consortium forms.
The layered architecture of blockchain is categorized into six layers.
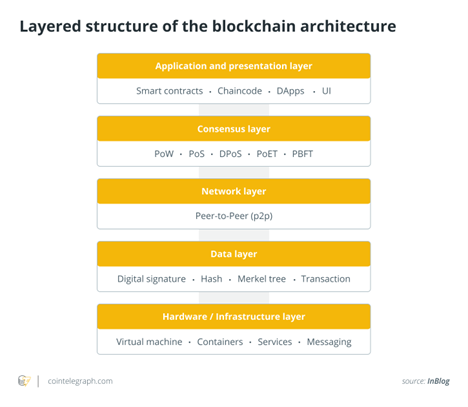
Hardware infrastructure layer
The blockchain’s content is stored on a server in a data center somewhere on this lovely globe. Clients request content or data from application servers while browsing the web or utilizing any apps, which is known as the client-server architecture.
Clients can now connect with peer clients and share data. A peer-to-peer (P2P) network is a large group of computers that share data. Blockchain is a peer-to-peer network of computers that computes, validates and records transactions in an orderly manner in a shared ledger. As a result, a distributed database is created, storing all data, transactions, and other pertinent data. A node is a computer in a P2P network.
Data layer
A blockchain’s data structure is expressed as a linked list of blocks in which transactions are ordered. The data structure of the blockchain consists of two fundamental elements: pointers and a linked list. A linked list is a list of chained blocks with data and pointers to the previous block.
Pointers are variables that refer to the position of another variable, and a linked list is a list of chained blocks with data and pointers to the previous block. The Merkle tree is a binary tree of hashes. Each block contains the root hash of the Merkle tree and information like the preceding block’s hash, timestamp, nonce, block version number and current difficulty goal.
For blockchain systems, a Merkle tree provides security, integrity, and irrefutability. The blockchain system is built on Merkle trees, cryptography, and consensus algorithms. Because it is the first in the chain, the genesis block, i.e., the first block, does not contain the pointer.
To protect the security and integrity of the data contained in blockchain, transactions are digitally signed. A private key is used to sign transactions, and anyone with the public key may verify the signer. The digital signature detects information manipulation. Because the data that is encrypted is also signed, digital signatures ensure unity. As a result, any manipulation will render the signature invalid.
The data cannot be discovered because it is encrypted. It cannot be tampered with again, even if it is caught. The sender’s or owner’s identity is also protected by a digital signature. As a result, a signature is legally linked to its owner and cannot be disregarded.
Network layer
The network layer, commonly referred to as the P2P layer, is responsible for inter-node communication. Discovery, transactions, and block propagation are all handled by the network layer. Propagation layer is another name for this layer.
This P2P layer ensures that nodes can find one other and interact, disseminate, and synchronize to keep the blockchain network in a legitimate state. A P2P network is a computer network in which nodes are distributed and share the workload of the network to achieve a common purpose. The blockchain’s transactions are carried out by nodes.
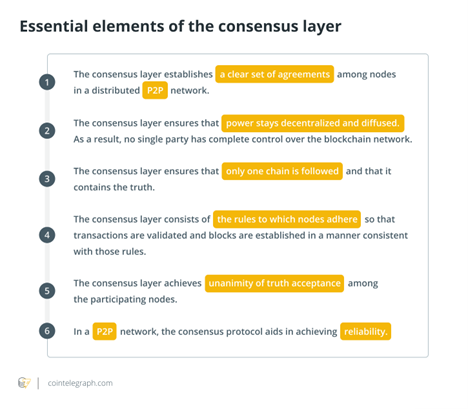
Consensus layer
The consensus layer is essential for blockchain platforms to exist. The consensus layer is the most necessary and critical layer in any blockchain, whether it is Ethereum, Hyperledger or another. The consensus layer is in charge of validating the blocks, ordering them, and guaranteeing that everyone agrees.
Application layer
Smart contracts, chaincode and decentralized applications (DApps) make up the application layer. The application layer protocols are further subdivided into the application and the execution layers. The application layer comprises the programs that end-users utilize to communicate with the blockchain network. Scripts, application programming interfaces (APIs), user interfaces and frameworks are all part of it.
The blockchain network serves as the back-end technology for these applications, and they communicate with it via APIs. Smart contracts, underlying rules and chaincode are all part of the execution layer.
Although a transaction moves from the application layer to the execution layer, it is validated and executed at the semantic layer. Applications give instructions to the execution layer, which executes transactions and ensures the blockchain’s deterministic nature.
Read our related article: Get A Complete Layer 1 Vs Layer 2 Blockchain List Of 2022 With Crypto Protocols Project Comparison | What’s The Difference
Blockchain Layers Explained
Layer 0
Blockchain layer zero is made up of components that help to make blockchain a reality. It’s the technology that allows Bitcoin, Ethereum, and other blockchain networks to function. Layer 0 components include the internet, hardware, and connections that will enable layer one to run smoothly.
Layer one
This is the foundation layer, and its security is based on its immutability. The Ethereum network, or layer one, is what people allude to when they say Ethereum. This layer is in charge of consensus processes, programming languages, block time, dispute resolution, and the rules and parameters that maintain a blockchain network’s basic functionality. It is also known as the implementation layer. Bitcoin is an example of a layer one blockchain.
Problems with layer one
These scaling solutions boost the network’s throughput when used together. However, with the growing number of blockchain users, layer one appears to be falling short. The archaic and clumsy proof-of-work consensus process is still in use on the layer one blockchain.
While this approach is more secure than others, it is limited by its speed. Miners are required to solve cryptographic algorithms using computational power. As a result, more computational power and time are required in the long run. Also, the workload on layer one blockchain has increased as the number of users has grown. Processing speeds and capacities have slowed as a result.
Possible solutions
Proof-of-stake is an alternate consensus that Ethereum 2.0 will adopt. This consensus approach certifies new transaction data blocks based on the staking collateral of network participants, resulting in a more efficient procedure.
Sharding is a scaling solution for the burden on the layer one blockchain problem. Simply said, sharding divides the task of validating and authenticating transactions into smaller, easier-to-manage chunks. As a result, the workload can be distributed over the network to use more nodes’ computing capability. Because the network processes these shards in parallel, several transactions can be processed both sequentially and simultaneously.
Layer Two
The overlapping networks that sit on top of the base layer are known as L2 solutions. Protocols make use of layer two to increase scalability by removing some interactions from the base layer. As a result, smart contracts on the primary blockchain protocol only deal with deposits and withdrawals and ensure that off-chain transactions follow the regulations. Bitcoin’s Lightning Network is an example of a layer two blockchain.
So, what is the difference between layer one and layer two blockchain? The blockchain is the first layer in a decentralized ecosystem. Layer two is a third-party integration used in conjunction with layer one to enhance the number of nodes and, as a result, system throughput. Many layer two blockchain technologies are being implemented at present.
Layer two scaling solutions
Layer two protocols have exploded in popularity in recent years, and they’re proving to be the most effective approach to solving scaling issues in PoW networks, in particular. Various layer two scaling solutions are explained in the sections below.
Nested blockchain
A nested layer two blockchain runs on top of another. In essence, layer one establishes the settings, whereas layer two conducts the procedures. On a single mainchain, there might be several blockchain tiers. Consider it a typical business structure.
Rather than having one person (e.g., the manager) conduct all the work, the manager delegated tasks to subordinates, who then reported back to the management when they were finished. As a result, the manager’s workload is reduced while scalability is improved. The OMG Plasma Project, for example, works as a level two blockchain for Ethereum’s level one protocol, allowing for cheaper and faster transactions.
State channels
A state channel improves total transaction capacity and speed by facilitating two-way communication between a blockchain and off-chain transactional channels via various approaches. To validate a transaction over a state channel, the miner does not need to be involved right away.
Instead, it’s a network-adjacent resource that’s protected via a multi-signature or smart contract mechanism. The ultimate “state” of the “channel” and all its inherent transitions are posted to the underlying blockchain when a transaction or batch of transactions is completed on a state channel.
State channels examples include Bitcoin Lightning and Ethereum’s Raiden Network. In the trilemma tradeoff, state channels give up some decentralization in exchange for increased scalability.
Sidechains
A sidechain is a transactional chain that runs alongside the blockchain and is used for massive bulk transactions. Sidechains have their consensus method, which can be adjusted for speed and scalability, and a utility token is frequently utilized as a part of the data transfer mechanism between side and main chains. The main chain’s principal function is to provide general security and dispute resolution.
In several important ways, sidechains differ from state channels. To begin with, sidechain transactions are not private between participants; instead, they are published openly on the ledger. Furthermore, security breaches on sidechains do not affect the mainchain or other sidechains. Building a sidechain from the ground up necessitates a significant amount of time and work.
Rollups
Rollups are layer two blockchain scaling solutions that perform transactions outside of the layer one network and then upload the data from the transactions to the layer two blockchain. Layer one can keep rollups secure because the data is on the base layer.
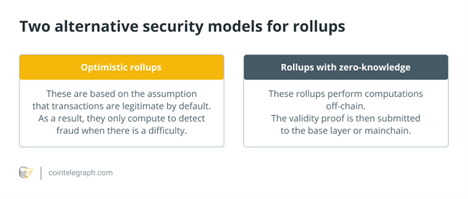
Users benefit from rollups since they help to boost transaction throughput, open participation, and lower gas costs.
Layer Three
The application layer is often referred to as layer three or L3. The L3 projects act as a user interface while masking the technical aspects of the communication channel. L3 applications are what give blockchains their real-world applicability, as explained in the layered structure of the blockchain architecture.
Read our related article: Complete Layer 3 Crypto Coins List & PDF 2022, What Is Web3 | Top 5 Investment Worthy Projects
Can the blockchain trilemma be solved?
The issues faced by distributed data storage, from which blockchains arose, were passed down to blockchains. To better comprehend these difficulties and related problems, the term “blockchain trilemma” was coined to group them.
Even though the word “trilemma” has remained, the blockchain trilemma is merely a conjecture. This hypothesis is suspected to be accurate based on early data, but it has been neither proved nor disproved. More research needs to be done, even though layer one and layer two solutions have already had some success.
The bottom line
One of the reasons why crypto mainstream adoption is now impossible in the blockchain business is scalability. As the demand for cryptocurrencies grows, so will the pressure to expand blockchain protocols. Because both blockchain levels have their own set of restrictions, the eventual solution will be to develop a system that can solve the scalability trilemma.
Layer one is critical since it serves as the foundation for decentralized systems. The underlying blockchain’s scalability issues are addressed via layer two protocols. Unfortunately, most layer three protocols (DApps) currently run only on layer one, bypassing layer two. It’s no surprise that these systems aren’t performing as well as we’d want.
Layer three applications are essential because they help to develop real-world use cases for blockchains. They will, however, not capture nearly as much value as their foundation blockchain, in contrast to legacy networks.
Get the complete Layer 1 Blockchain PDF
Get the complete Layer 2 Blockchain PDF
Get the complete Layer 3 Blockchain PDF
Originally published via this site
Although the material contained in this website was prepared based on information from public and private sources that LCXwire.com believes to be reliable, no representation, warranty or undertaking, stated or implied, is given as to the accuracy of the information contained herein, and LCXwire.com expressly disclaims any liability for the accuracy and completeness of the information contained in this website.
About LCXwire
LCXwire is dedicated to providing you the latest news about the products and services of the Liechtenstein Cryptoassets Exchange, the LCX token, and information relevant to the Centralized and Decentralized Finance (CeFi and DeFi) Exchanges. Our goal at LCXwire is to provide you with the best, most relevant and exclusive information about the crypto industry.
Follow us: Facebook I Facebook Groups I LinkedIn I Twitter